What Phishing Campaigns Have in Common with the Cocos Islands?
Phishing is one of the main reasons why Australian businesses are getting hacked. What has an exotic paradise in the middle of the Indian Ocean to do with cyber crime? Iron Bastion experts explain how Cocos (Keeling) Islands enables criminals to defraud organisations and individuals worldwide.

Phishing is one of the main reasons why Australian businesses are hacked. So what does an exotic paradise in the middle of the Indian Ocean have to do with global cyber crime? We explain how Cocos (Keeling) Islands enables criminals to defraud organisations and individuals worldwide.
Phishing Campaigns Require Domain Names and Web Hosting
For every successful phishing email campaign, criminals require a domain name for sending emails and hosting the associated services such as fake login pages.
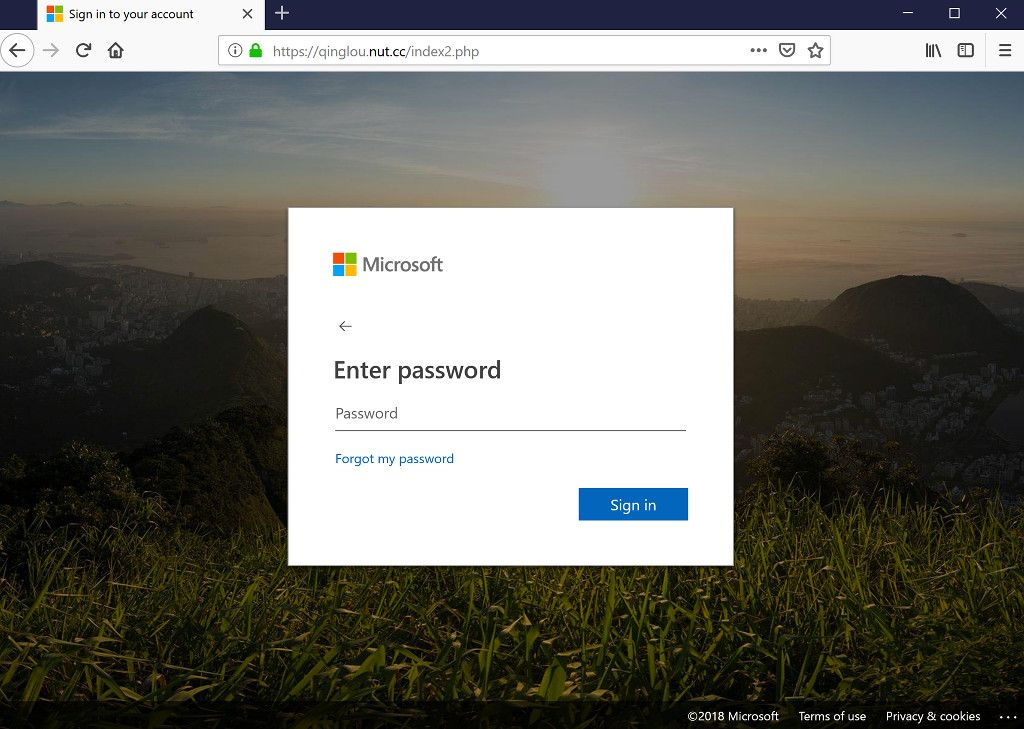
Probably everyone has seen a perfect clone of the Office 365 login page that looks like the genuine one at Microsoft. Often, the only difference between the fake and real one is the address in the URL bar of the web browser. Apart from that, everything else looks perfectly the same. Needless to say, any login password entered on these clones go straight to the criminals instead of the real service at Microsoft.
Phishing emails stealing Office 365 login passwords are getting more sophisticated.
— Iron Bastion (@IronBastionAu) October 25, 2018
This one claims that 8 messages are held up in a quarantine due to 'system mail delivery malfunction'. The link beneath the 'Release to Mailbox' button leads to a fake Office 365 login page. pic.twitter.com/fN3ttx3BHv
For running a phishing campaign like this one stealing Office 365 login passwords, criminals usually require either:
- An existing domain name (i.e. hacking an established website to swap the web pages with the fake login pages); or
- A brand-new domain name and their own web servers for hosting the deceptive content.
Both options have their advantages. As for using an existing domain name, emails with trusted domain names are less likely to be captured by spam and anti-phishing filters making those campaigns more successful. The disadvantage is that the owners of the hacked websites can take the phishing site down at any minute. For this reason, criminals need a constant supply of compromised web servers to keep their phishing campaigns going.
On the other hand, newly registered domain names do not have this supply chain issue. Bad actors can simply register domain names of their choice that resemble a brand they wish to impersonate. The shortcoming of fresh domain names is the lack of reputation. However, it is a common anti-phishing technique to block emails and access to websites associated with newly registered domain names. However, phishers often get around of this practice by waiting weeks or even months before using domain names they have registered for phishing.
Criminals Prefer Web Links over Malicious File Attachments
The explanation behind the massive demand for domain names within criminal circles is simple. Bad actors prefer web links pointing to fake, password-stealing login pages (under their control), over files and document attachments with a virus and other malicious code embedded inside.
The latest trend is that the majority of phishing emails features a web link rather than a file attachment. Industry reports confirm that only one in every five phishing emails contain a malicious file attachment, while one in every two (53%) features an embedded web link pointing to malicious content hosted somewhere.
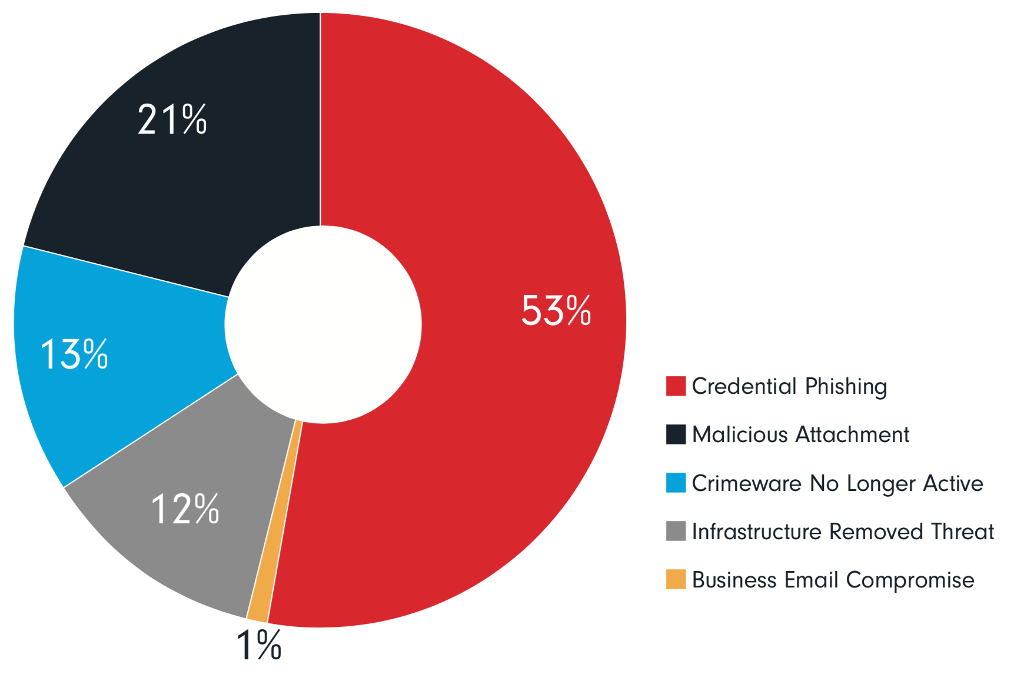
With the advent of cloud-based services, businesses tend to store their files, email correspondence, address books and customer lists on the internet. This is why a stolen password giving access to a business's Office 365 or Dropbox account is far more valuable than a computer compromised with a piece of malware or ransomware.
More convoluted scams go further than selling the stolen login credentials on the dark web and using the compromised email accounts for innocuous things like spamming. Real criminals go as far as tampering with payment instructions within the incoming or outgoing emails of a compromised email account with the intention of scamming hundreds of thousands of dollars out of their victims.
For instance, a former Masterchef contestant in Australia was a victim of a highly publicised business email compromise fraud whereby her family was left homeless. As it transpired, the family’s conveyancer had their email hijacked by a cybercriminal leading to the theft of $250,000 by the criminal redirecting settlement funds.
Why Exotic Top-Level Domains Are Popular in Phishing Campaigns
According to the Anti Phishing Working Group report from last year, the most popular top-level domains (TLD) for hosting phishing sites are: .com (58%), .cc (14%), .pw (3%) and .tk (3%). The .com domain choice seems plausible, but what makes .cc the second most popular one?
First of all, the visual similarities make the .cc domain ideal for impersonating legitimate brands with a website on the .com domain. It is relatively easy to mistake paypal.cc for the real one at paypal.com when only the last two characters are the only difference in a long URL.
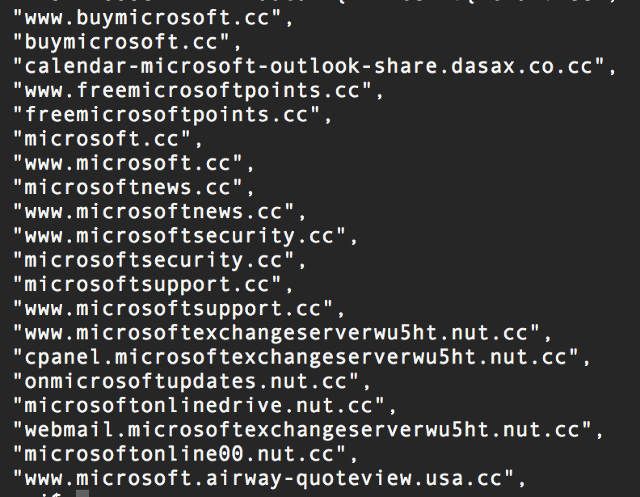
This practice is similar to criminals operating and/or targeting victims in China. According to the Anti-Phishing Alliance of China, bad actors often impersonate Chinese brands (e.g. banks) hosted on the .cn TLD by registering a similar-sounding name on the .cc or .cf variation.
Lack of Regulation Is a Hotbed for Domain Abuse
Why has nobody steps in to stop websites popping up on these often abused top-level domains? Reasons include the lax or nonexistent oversight. Cocos (Keeling) Island (.cc), Tuvalu (.tv), Tokelau (.tk) are all small islands where the income from domain registration fees are a vital part of the local economies.
For example, two of Tuvalu's main revenue stream are:
- Fishing (the real one!) licence sales; and
- The royalties from the sale of the .tv domain.
In 2010, almost 10% of Tuvalu's income came from the fees associated with the .tv address. Similarly, domain registration fees also play a significant role in the Cocos Islands where the local population is fewer than 600 people.
Apart from economic reasons, peculiarities around abuse policies can explain the popularity of these TLDs. Countries like Cocos Islands have outsourced the domain registration business to a private company called Verisign with little to no oversight over the domain registration process.
While auDA (a not for profit organisation) is the policy authority and industry self-regulatory body for Australia (.au), the .cc domain is regulated by the same private company responsible for the domain registrations. Interestingly, the administrative contact for the .cc top-level domain is an email address belonging to Verisign. In plain English, the regulatory body is the very same company selling .cc top-level domains.
The scale of the abuse involving .cc top-level domains was so extensive that in 2011 Google removed more 11 million websites hosted under the .co.cc subdomain as a drastic measure. The .co.cc subdomain registry offered single sub-domains for free and enabled its customers to bulk-register 15,000 addresses at a time for a mere U$1,000, or about seven cents a pop. Other non-official and frequently abused services offering free subdomain registration are cc.cc, cu.cc, and cz.cc.
Conclusion
Cybercriminals have many tricks up their sleeves to deceive their victims into clicking on a web link or opening a file attachment. One of these techniques is registering lookalike internet domain names on alternative top-level domains for the sole purpose of masquerading as a legitimate brand. Some of the top-level domain registries have poor or no policy measures in place to prevent abuse, which makes these domains an ideal playground for organised criminals.
What is the takeaway? Experts at Iron Bastion suggest taking a vacation on the Cocos (Keeling) Islands, but be extra vigilant when receiving an email with the territory's domain name inside.