Owning Your Legal Practice's Cybersecurity – MSPs and You
Law practices should be aware of the cyber risks associated with IT, as a security breach involve financial and reputational damages, and legal liabilities. Read what the six questions are that every legal professional should ask from their managed IT services provider to avoid a data breach.

Information Technology, or IT, can increase a law practice’s productivity, enable higher quality services and facilitate client introductions and engagement.
It is imperative, however, that law practices – and small businesses in general – are aware of the inherent risks associated with IT, as financial and reputational damage due to hacking, data loss and other adverse events has put some legal practices out of business.
For example, if your practice relies on email for communication, your business is potentially exposed to phishing, business email compromise fraud, payment redirection scams and ransomware. In more sophisticated cases, hackers can impersonate you and your practice to your clients and email them fake invoices, or bogus payment directions.
Consequences of security breaches
If you have other IT systems to support your business, such as a customer relationship management (‘CRM’) platform or practice management software, the immediate damage to your practice from a cyber attack against those systems could include:
- hackers misdirecting trust money, funds held in an office account or settlement funds;
- interruptions to normal business operations;
- unexpected expenses related to remediation of systems, such as hiring high-paid security consultants, performing expensive data-recovery, or repairing/replacing systems post- breach.
The long-term consequences of a cyber attack against your IT systems could potentially include:
- damage to your practice’s reputation;
- loss of existing and future clients;
- unwanted media attention;
- legal action against you by your clients for professional negligence or other claims, such as breach of trust.
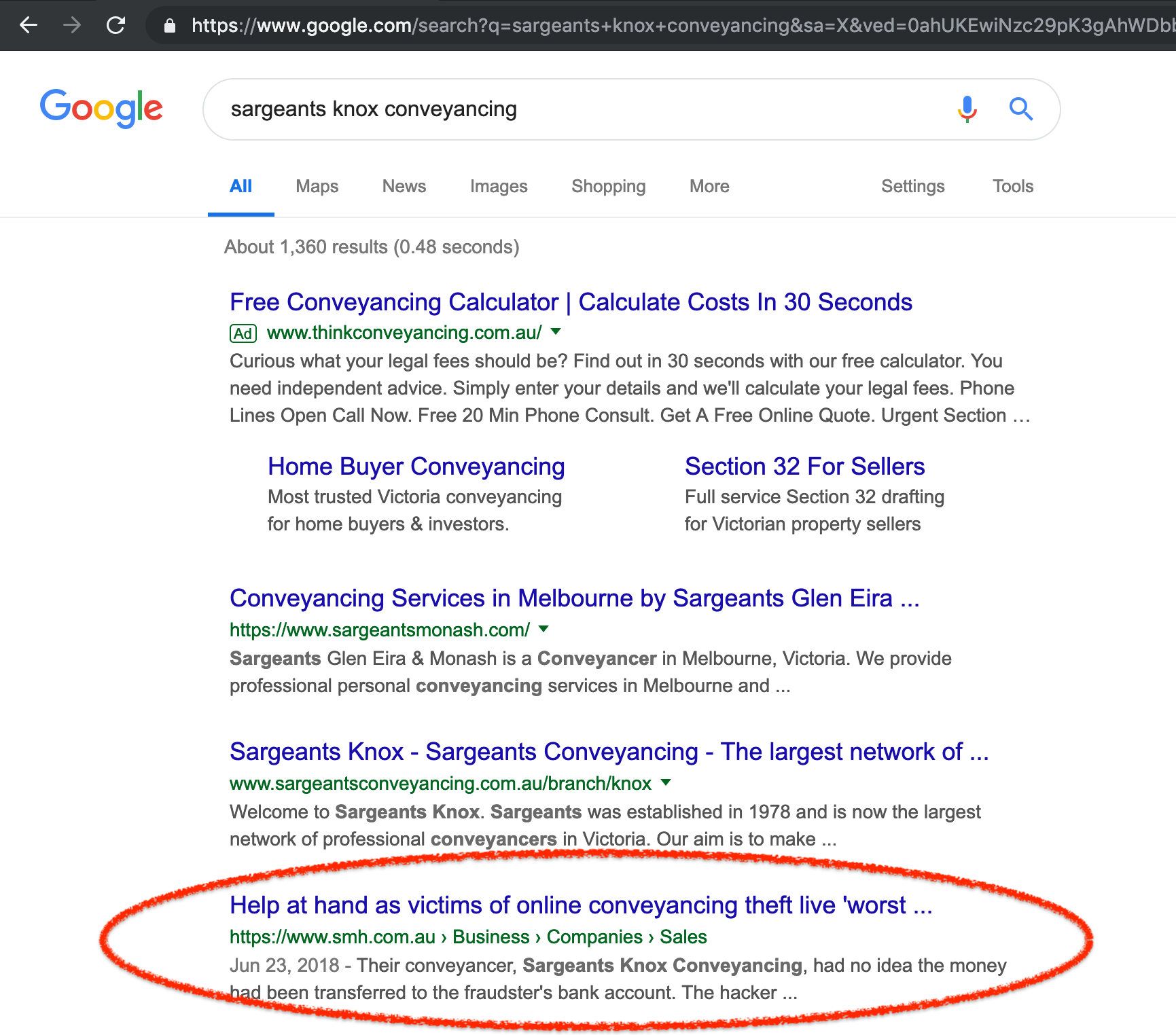
General guidance on improving the overall security posture of your firm is available from best-practice cyber frameworks such as the Essential Eight Maturity Model or Malicious Email Mitigation Strategies, both maintained by the Australian Cyber Security Centre (‘ACSC’). Practices may also wish to hire cyber security experts or consulting firms that can better identify and mitigate the relevant security risks in the context of the practice's unique environment.
Outsourcing of IT services
Most practices engage IT experts to set up and manage IT services. Depending on size, law practices usually have the choice between employing someone to maintain IT for the practice, or outsourcing it to a Managed Service Provider ('MSP').
MSPs provide a range of general-purpose outsourced IT services tailored for different markets and clients. IT providers catering to larger organisations provide services including email, backups, on-premises servers and security coverage. Small to medium-sized businesses are likely to receive website hosting, email hosting, domain name management, antivirus protection and general desktop support.
There are practical reasons why many law firms hire MSPs rather than keeping IT in-house. Firstly, practices can benefit from the arrangement through lower costs. MSPs usually have mutually beneficial agreements with vendors and suppliers allowing them to purchase software and services for a lower price which can be passed on to clients and economies of scale by servicing a large number of businesses.
Second, MSPs also have the accumulated experience to build and operate complex IT environments as opposed to in-house staff. In comparison, developing an internal IT function requires an organisation to hire, train and manage staff.
Risks associated with MSPs
While MSPs are responsible for managing all sorts of IT challenges including security, for MSPs maintaining availability and user experience can compete with optimising cyber security. On the other hand, lawyers’ strict duties to act as trustees and maintain confidentiality means that security is critical. Legal and professional obligations to maintain confidentiality and privacy remain with the law practice even when an external entity manages IT.
It is a common misconception that IT is a ‘set and forget’ function, especially when a third-party is hired to manage IT. However, the reality is that having a managed service provider can also introduce new risks.
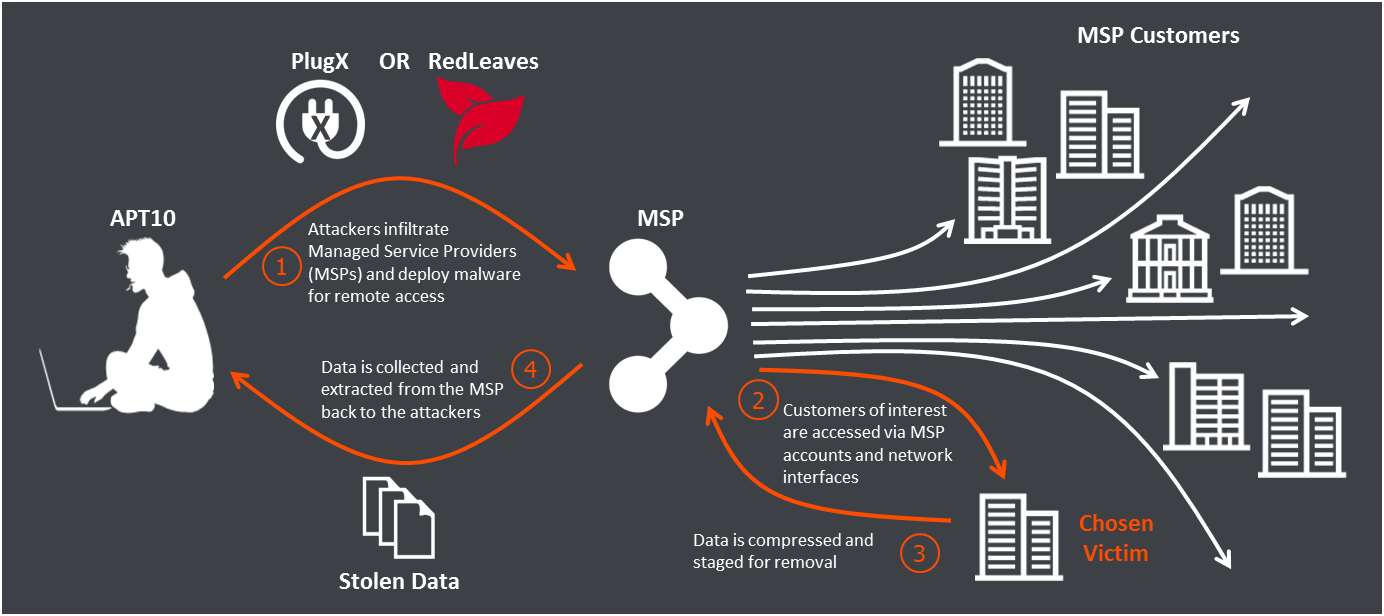
For instance, cyber criminals intending to defraud practices often take the course of optimal return by hacking MSPs first. According to the ACSC: ‘Many of the compromises involving customers of MSPs occurred because MSPs themselves were the initial point of compromise. That is, the customer was not the initial victim; the MSP was the vector to compromise their customers.’
This practice fits into a global trend of supply chain attacks, where criminals target IT systems through trusted vendors rather than attacking them directly.
In parallel, the goal of any MSP may be delivering a range of services as laid out by service agreements, meaning that usability, availability and customer experience might be preferred over more stringent cyber security. This different focus could potentially lead to a conflict of interest.
For example, anti-phishing solutions may delay or block the arrival of legitimate emails by holding them up for inspection, resulting in a poor customer experience when compared to systems using no protection. Although this can be a reasonable trade-off between convenience and security, MSPs may make security decisions that are different to those a law practice would choose, so it is advisable to discuss your risk appetite with your IT partner rather than assume your MSP has made optimal technology choices to protect your business from cyber threats.
Other areas of potential conflict
There are other areas in which the interests of the law practice and MSP may not align. For example, an IT provider might have commercial reasons for preferring a specific brand of antivirus product instead of choosing a product that best enhances security.

Software packages are usually discounted as part of a licence package, so an antivirus product that is part of a discounted bundle might be missing advanced security features that provide more sophisticated protection against threats such as phishing and ransomware.
It is therefore prudent to ask your provider about this issue, preferably in writing, and if appropriate ask for a second opinion from a cyber security expert.
Factors to consider
The circumstances that each practice should consider when deciding on appropriate levels of cyber security include:
- the value the practice's data would have for cyber criminals, noting that tax file records, identity documents, medical records and confidential commercial documents are particularly valuable;
- identifying who has access to the data, how it is protected, and the location where the data is held (in particular, whether the data could be subject to another legal regime);
- current or emerging cyber threats to the legal services sector.
Be aware that the contractual arrangements between your practice and the MSP may also be relevant when considering liability issues in the event of a cyber breach.
Further, any contractual terms that operate to extend your duty beyond the usual standard of a lawyer in the same circumstances, or which increase the compensation or damages for which you are liable for breach of duty, could trigger an exclusion clause under your professional indemnity insurance policy in the event of a third party claim against you.
Questions to ask your MSP
In December the head of the ACSC announced that thousands of Australian companies may have been impacted as a result of the alleged hacking of major global technology firms by a group connected with Chinese intelligence services. Governments including the UK, Canada and Australia reported adverse campaigns against global MSPs which targeted intellectual and commercially sensitive information held by the affected MSPs and their clients.
In response the ACSC has recently published a simple guide for small business owners to combat the growing number of supply chain attacks through MSPs. This document recommends that every small business asks its managed IT service provider the following:
- Are you implementing best practice cyber security guidance?
- Are you regularly assessing our cyber security posture?
- Are you protecting your access to our systems?
- Are you protecting users from socially engineered emails (i.e. phishing)?
- Are you backing up our data?
- Are you prepared for, and actively reporting, cyber security incidents?
For further information see: cyber.gov.au/business/publications/msp-questions-for-msps/MSP_Questionnaire.pdf
Key Insights
- Professional obligations to maintain confidentiality and privacy cannot be outsourced to IT providers and Managed Service Providers (‘MSPs’).
- Be proactive in understanding your practice’s cyber security profile – do not regard it as a ‘set and forget’ issue.
- Consider obtaining external help to identify cyber/IT risks where appropriate.
This is a revised version of an article co-written by Simone-Herbert Lowe and Gabor Szathmari for the Law Society Journal. Simone is a solicitor and director of Law & Cyber Pty Ltd and Gabor is a cyber security expert and director of Iron Bastion Pty Ltd and Arrow Networks.